How To Build
a Bullet-Proof Digital Privacy
and User Authentication?
New Wave of Encryption Technologies
For Security Cameras and Streaming Videos
Consumer Privacy Acts
CCPA 5 Rights & CPRA
Since Jan. 2023 in California
The right to opt out of
certain uses and disclosures of
“sensitive personal information.”
General Data Protection Regulation
Data Security Measures
For Accountability to Data Privacy
GDPR 7 Principles
growing GDPR Penalties
Since April 2016
GDPR requires data subjects to opt in.
Personal Information Protection Acts
Regulate the collection,
usage, disclosure,
and other processing of personal data
Known as one of the strictest sets of data protection laws in the world.
Since 2011, South Korea
Smartphone protection
messages, photos, and personal data
Authentication
Identity & access management,
Authenticate Passport, ID, Certificate, Membership, Credit Card, Gift Card, Coupon, Product, and protection from counterfeits
Secure Protection
Unauthorized Copies, hacking and distribution of consumer data, Credit card and confidential digital assets
Understand Limitations
of current Encryption Technologies
For Security Cameras and Streaming Videos
Secretize
Private
Sensitive
Confidential Data &
Digital Assets
Secure Data Sharing
Millions of people are exposed
to the high risk of private data breaches
when they exchange information, messages, emails, photos, videos, and documents every day
through smartphones, computers, social media, e-commerce, and an increasing number of surveillance cameras.
How to secure your digital privacy?
From security cameras, videos, messages, documents, private photos, and sensitive data after they are captured.
Build A Data Security Roadmap
data security 101
Protect critical assets
☑ Policy & governance of data security
☑ Identification of critical assets
☑ Access control | IDPS
☑ Incident Handling Procedure
☑ Data Stewardship Training
Layers of Security
Protective Measures
of Data Breach Incidents
☑ Authentication
☑ Encryption
☑ Pseudonymization
☑ Anonymization
☑ Obfuscation
☑ Sanitization
☑ Multi-Layered security with Key Management
%
of Chief Security Information Officers do not know where the critical data asset is
Totally New Way Of
Data Privacy Protection of
Security Camera,
Streaming Video Conferencing,
and Digital Privacy Compliance & Protection

Digital Transformation with Data Security
Build a strong digital transformation roadmap with digital privacy protection as an extra layer of security
Consumer Privacy and Protection From Data Breach
Protect data breach from smartphone, personal smart devices, finance and banking information
Corporate Digital Asset Protection for IT Management
Protect form unauthorized copy, download, and secure sharing of confidential digital assets and information
%
of consumers say it is "Extremely Important" that companies quickly take the right actions to stop a privacy data breach.
%
of consumers think government should do more to protect data privacy. Social Media sites are the least trusted, followed by travel and retail industries.
Faster, Flexible and Strong Data Breach Protection.
Convert Text, Images, and Sensitive Digital Assets into
Obfuscated Cryptographic Image shuffling for Secure Exchange,
Only readable to Authorized recipients and environments.
Payload Protection of Transmitted Data.
Powerful True Authentication & identify security from Counterfeits.
Compliance and Accountability of
Consumer Privacy Acts and General Data Protection Regulation
for Corporate IT Managers & Consumer Privacy
Secure Protection
Unauthorized Copies, Downloads and Hacking of Sensitive Data, Images, and Confidential Document
Authentication
True Identity & Access, Title, Certificate, Gift Card, Mobile ID, Genuine Product ID, Copyrighted Materials, Corporate Document.
Secure Exchange
Email, RCS, SMS, social media sharing of private messages, photos and copyrighted content
User-initiated Security | Secure Exchange of Confidential Data & Authentication | Flexible Security Layers

Digital Platform with Data Security

Consumer Privacy and Private Data Breach Protection of e-Commerce, Smart Device and Autonomous Driving Platform

Sensitive Data Protection of
Smart IOT and Big Data Appliance, and AL/ML/DL Ecosystem
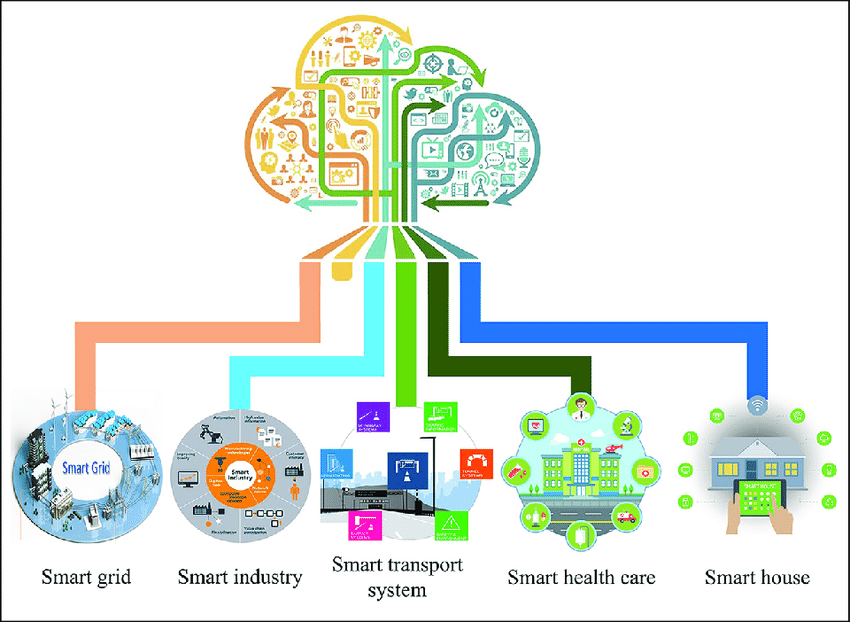
Unauthorized Access and Data Breach of Artificial and Human Intelligence Platform and Privacy Intelligence

Digital Transformation with Data Security, Integration and Fulfillment Services and Authentication from Counterfeits
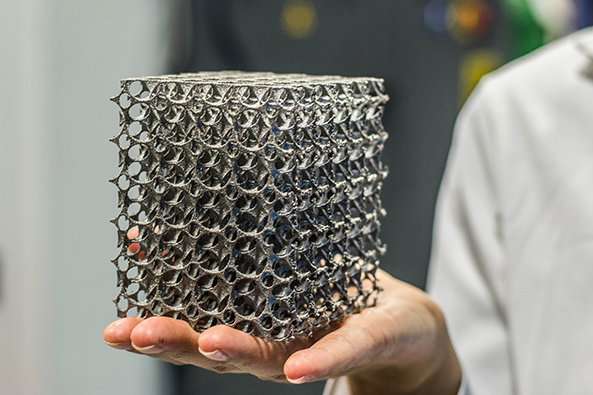
Digital Asset Security and Unauthorized Copy Protection of R&D Data of Industry 4.0 and Additive Manufacturing

Testing, Integration of Consumer Privacy Applications and Big Data Appliance with Data Security
